Wireless Network Bridging with Security in a Home or Small Business
Sometimes a home or small business would like to extend a network without running any ethernet cables or using expensive power line methods. Many homes have an old WiFi router that is still working, but the new router still doesn’t get signal to all parts of the home or some devices do not support WiFi networking, only 100base-tx wired. By using the new WiFi router with the older WiFi router, it is possible to extend a network over WiFi and locate wired connections on the far side of the home using just the two wifi routers in bridge mode.
Here’s a simple network design for a home or small business that uses WiFi bridging to extend the network while keeping the high risk devices on a different subnet than the more important devices. Guides for how to specifically configure a WiFi network bridge are available, but do not usually include a good network diagram. Here’s my take on that.
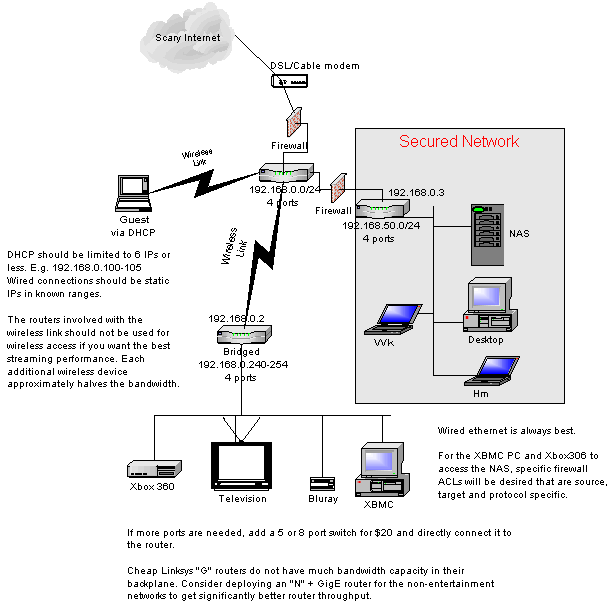
The Secured Network can have WiFi enabled too, just be certain it follows my WiFi Security Checklist. Additionally, don’t tell the guests the WPA-AES passphrase. Guests and children should not be allowed on the protected network.
Different Opinions
As usual, there are many different ways to accomplish the same end goal and different people will have different opinions about the setup or complexity. That diagram is simply my way of doing it.
Performance
To get better performance, the main router should be a newer Gigabit router so the backplane will be able to support the additional bandwidth requirements from all the systems. I’d use a gigabit “N” wifi router for the protected network too so the parent computers have the fastest possible connection between those systems.
WiFi Signal
Getting WiFi connections like this bridged connection to work on the far side of a home or business may require extra steps. Steps like, increasing the power, setting up parabolic antenna specifically between the two routers and carefully selecting WiFi channels for the least interference from other internal and external sources (neighbors). Some antenna options. It should be noted that for the newer WiFi systems with multiple antennas, you could easily reduce connectivity by attempting to add a parabolic reflector. For an older “B/G” router that doesn’t have mimo, this should be safe enough. Obviously, you may not need these extra steps and a small location change on either side can make a huge difference in the wifi connectivity.
High Risk Users
If there are teens on the network, I would definitely not allow their machines complete access to the Secured Network. Teens perform high risk behaviors on computers, just like with automobiles. The firewalls are shown as logical points where the flow of traffic can be limited to specific requirements, like streaming media from the NAS to the entertainment systems or backups of those systems to the NAS. Other systems that I’d keep from the Secured Network are any guest laptops.
I know that most home networks are not setup in this fashion, but perhaps they should be to help mitigate risks if they have any important data or high risk users?
Small Businesses
Private businesses that provide Free WiFi for their customers definitely need to separate the customers from their internal computer systems. This is for those businesses that don’t contract out the WiFi networking to another company – think Mom & Pop coffee houses, diners, or small bed and breakfast establishments. Protecting internal client and other business data is important for every small business, but you still want that free wifi sign outside to entice users inside who might just want to check email quickly and order a soda or coffee.
Feedback?
What did I get right and what did I get wrong? What would you setup differently?
Trackbacks
Use the following link to trackback from your own site:
https://blog.jdpfu.com/trackbacks?article_id=689

